Tiger Bridge
Intro
Tiger Bridge is a product of Tiger Technology. Tiger Bridge is a connector that creates a single namespace between different sources, and Cubbit Cloud Object Storage. It allows replication, tiering, and collaboration of unstructured data with file-locking capabilities between different file systems. Data is stored in Cubbit in native format. Tiger Bridge can be deployed on physical or virtual infrastructure and can be easily integrated within the existing environment.
Prerequisites
To set up Tiger Bridge with Cubbit, you first need to get your access and secret keys from the Cubbit Web Console or console.[tenant-name].cubbit.eu. You can follow the instructions provided to create a new Cubbit account and generate these keys. A new empty bucket with versioning enabled must be created. You will then need the latest release of Tiger Bridge software.
Installation
Tiger Bridge must be installed and fully configured on a Windows file server. Windows server must have access to a Cubbit storage account prepared in the previous step. Tiger Bridge can be deployed as a standalone hybrid configuration or as a multi-site configuration. The multi-site requires the "multi-site" license and all servers participating in the multi-site must have Tiger Bridge configured with the same settings pointing to the same Cloud storage configuration.
Standalone hybrid configuration
This installation will be repeated on every server part of a multi-site configuration. There are a few other parameters specific to the multi-site environments and they are described in the multi-site section of this document.
-
Installing Tiger Bridge on your Windows server. Installation is done by running the Tiger Bridge installation file and following the wizard. During installation, you can select two components:
- Tiger Bridge installs the product, GUI, and command-line interface.
- Shell Extension provides integration with Windows Explorer and allows manual management of the data through the Windows Explorer context menu.
-
In Tiger Bridge Configuration, add a local volume source:
- Select Tiger Bridge in the left pane
- Select Add Source
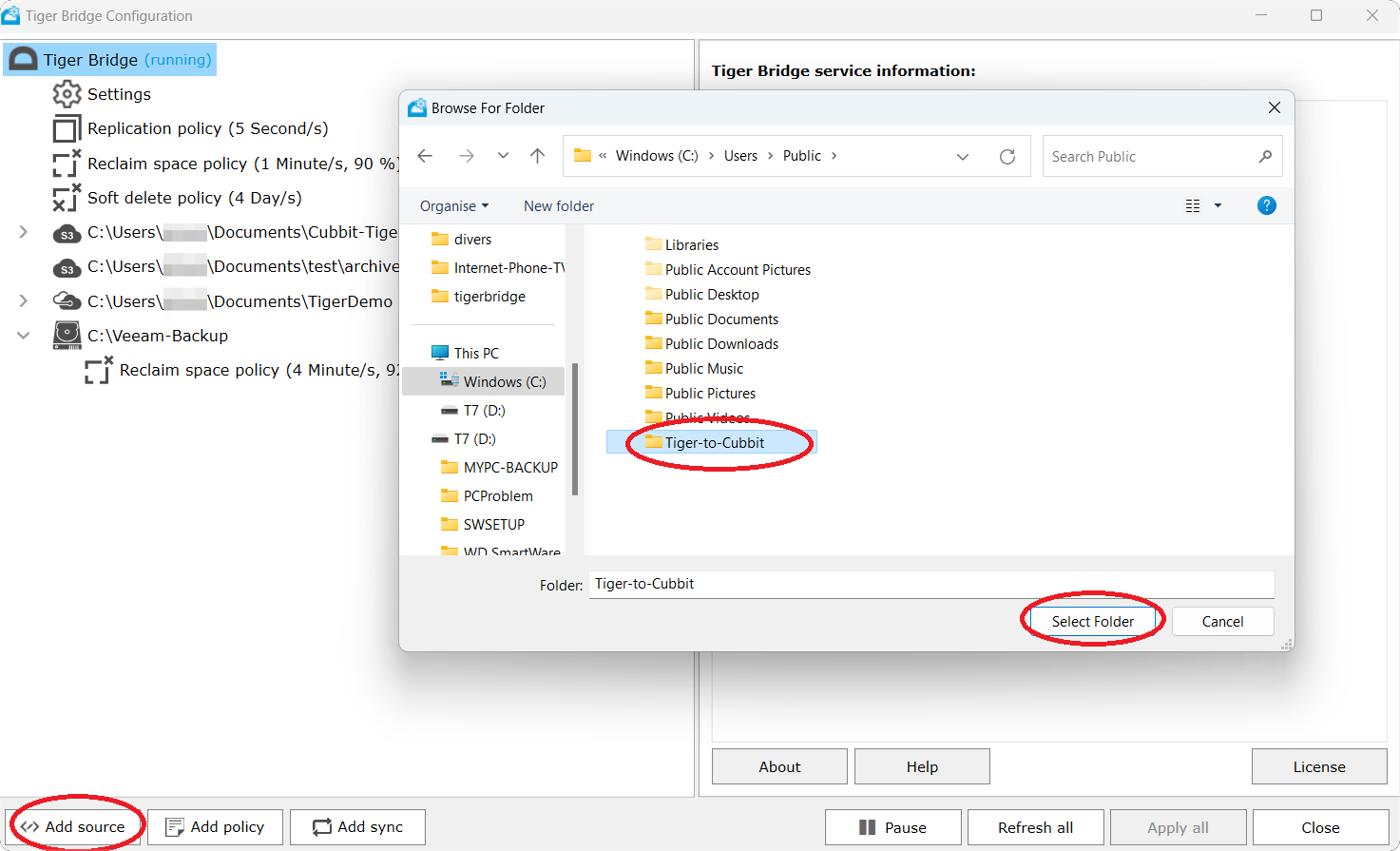
- Select the root of a drive, or browse to a folder you want to use for storing data.
- Select a folder and press OK. In this example, we will use the
C:\Users\Public\Tiger-to-Cubbitfolder.
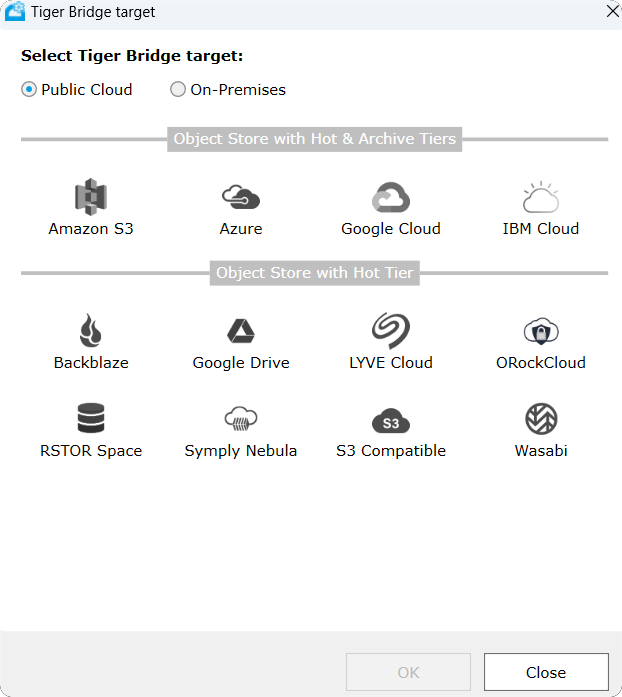
Once the source folder has been selected the target menu pops up and the S3 Compatible cloud must be selected, then press OK.
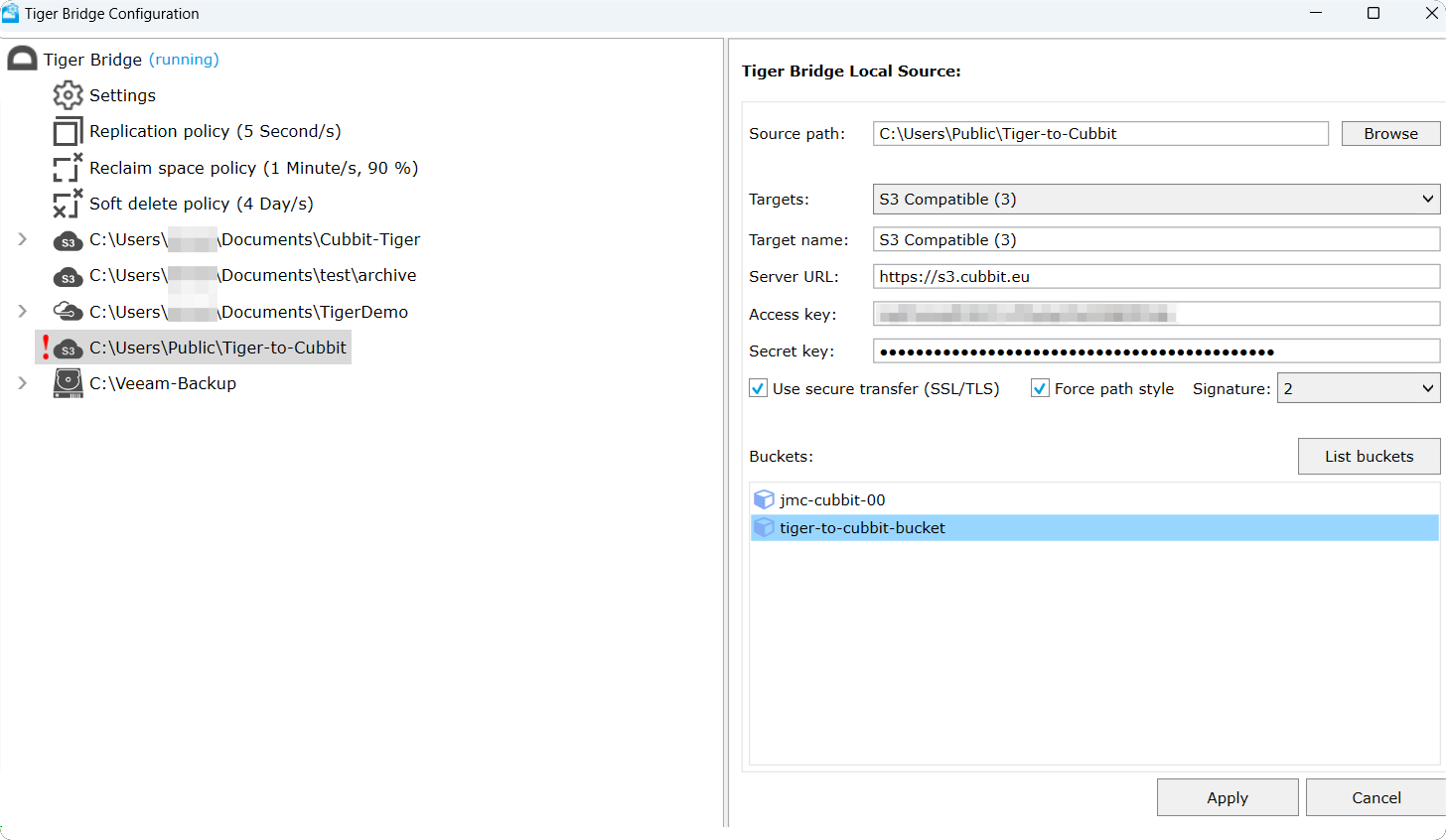
The Cloud menu is then displayed, and the following information must be provided:
- Cubbit S3 endpoint (here
s3.cubbit.euor if you have a custom tenants3.[your-tenant].cubbit.eu) - The access and secret keys created using the Cubbit Console.
Then click on List buckets and select the appropriate bucket.
In this example the bucket name is tiger-to-cubbit-bucket, select Apply.
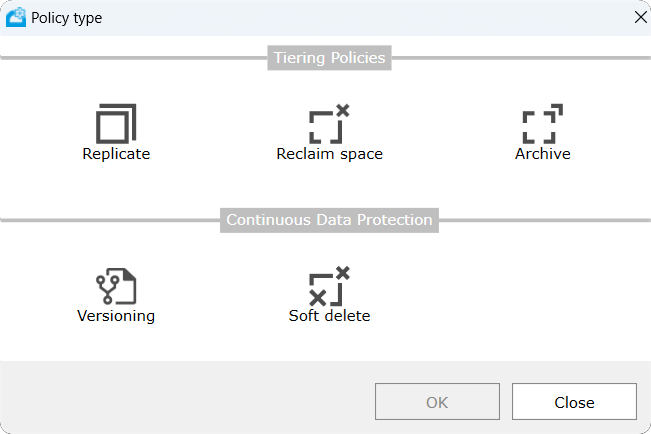
The following policies must be defined. Policies can be either global (they apply to all the defined sources), or local (applicable to a specific source) and will override the global policy if it exists.
Create a policy by selecting Add policy. Select the policy based on the use case requirements:
Replicate
This policy specifies when data are copied from the local source to the Cubbit bucket. Automatic replication is performed based on user-defined criteria.
Reclaim Space
This policy allows for reducing the on-prem storage used capacity, once data have been replicated to the Cloud storage. It replaces the data with a Stub file. A Stub file looks exactly like the actual file but doesn't contain any data (doesn't take up any space).
Archive
This policy does not apply to Cubbit Cloud Storage.
Versioning
To allow keeping versions of replicated files, versioning must be enabled both on the target and in Tiger Bridge. If either one is disabled each new copy of a replicated file overwrites the previous one.
Versioning is required to protect data against ransomware, as it will allow the restoration of a previous version of a file.
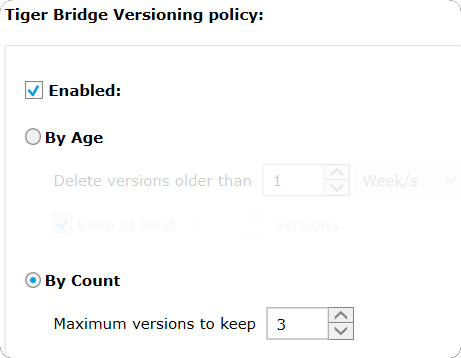
As long as versioning is enabled in Tiger Bridge, each new replica of a file is kept as a separate version on the target. To limit the number of replicas of the same file, Tiger Bridge allows to set the maximum number of versions via the versioning policy. Versioning policy must be enabled, and then the user will choose the most appropriate one. Versioning can be defined either during a given period or for several versions. The user must select the most relevant for the use case.
Here all versions are kept for one week, with a minimum of 2 versions:
While here a maximum of 3 versions are kept regardless of their age:
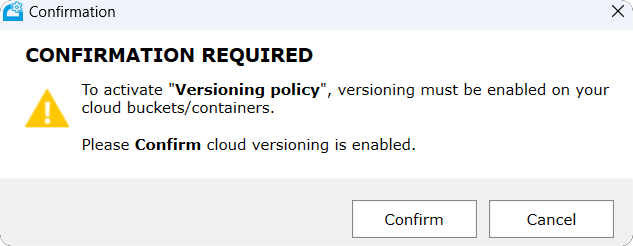
When versioning is enabled on Tiger Bridge, this requires that the bucket is also configured with versioning enabled. A warning reminds the user to make sure this is the case.
Soft Delete
Considering that S3-compatible Object Storage does not have a "recycle bin" to retain data deleted by mistake, the Soft Delete Policy specifies how long after a file is deleted from the source it should also be deleted from the target in case "Delete Replica when Source File is removed" has been enabled. The duration specified in the Soft Delete Policy will preserve the data during this period to recover accidentally deleted files. The example below shows extended granularity and the chosen option is 2 days:
Multi-site configuration
Tiger Bridge must be installed on all servers participating in the multi-site and the same configuration must be set for the Target Cloud. Tiger Bridge automatically synchronizes the contents of multiple sources, each on a different computer running Tiger Bridge, through a common target. The mechanism is designed to facilitate geo-replication scenarios.
The Synchronization is set at the folder policy level:
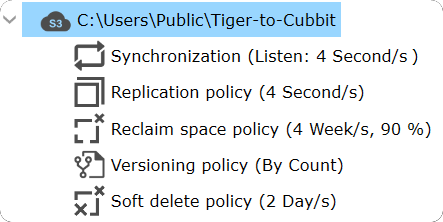
In such a multi-site environment it is recommended to set the replication and synchronization values to a few seconds (maximum 5 seconds). With multi-site the complete set of policies will appear as shown in the screenshot below:
Ransomware Protection
Tiger Bridge offers three methods of protecting your data from ransomware:
- Longer Replication Policy
- Fuse Defense
- Versioning
A longer retention policy, for example, 24 hours, gives the Tiger Bridge administrator 24 hours after a cryptovirus attack to detect the problem and recover. If the files in your source get encrypted, you can go to your cloud portal and download the copies that reside there. As long as you manage to do that within the replication policy time, in our case 24 hours, the files you download will be unencrypted and you will only lose the modifications introduced during this 24-hour wait period.
Fuse Defense: if ransomware affects many files at once, the replication queue will become abnormally high, if this threshold is exceeded Tiger Bridge will get paused. The administrator will be able to see the amount of modified and pending files within the directories by checking the properties of the folders in the source directory. The right value for this threshold depends on the customer's workload. The following screenshot shows the section of the settings, where Enable ransomware protection must be selected along with the number of files in the queue:
Versioning: This method provides versions of all modified files, and it is under administrator control to select which version has to be restored.
The combination of Fuse Defence and Versioning may require more cloud storage to keep new versions, when necessary, but it is the best option against ransomware attacks.
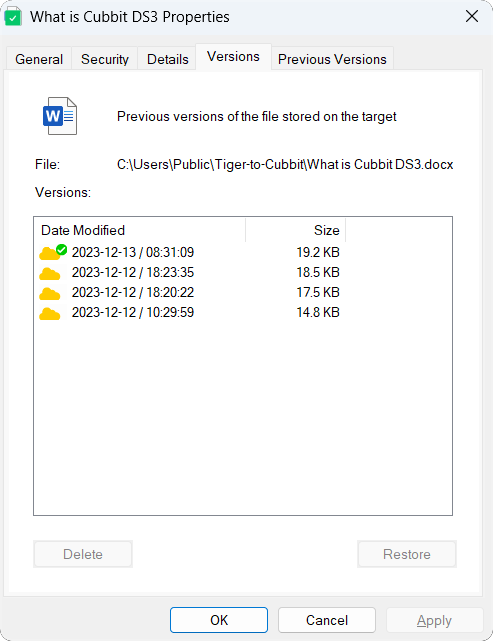
If a file appears to be encrypted, the user can select a previous version and restore it in place of the encrypted one by clicking on Restore, through the Tiger Bridge extension using Windows Explorer:
For more information on using Tiger Bridge, please visit the Tiger Technology official documentation page and select the latest release for both the Administration Manual and the release notes document.
For ransomware protection, download the Ransomware Protection with Tiger Bridge documentation.