CloudFront
Intro
CloudFront, developed by Amazon Web Services (AWS), is a cutting-edge content delivery network (CDN) that plays a pivotal role in shaping the modern web experience. This distributed service optimizes the delivery of static and dynamic web content to users by caching and serving data from geographically dispersed edge locations. By leveraging advanced caching, request routing, and global presence, CloudFront ensures ultra-fast content delivery, reducing latency and improving website performance. Its security features encompass SSL/TLS encryption, protecting content in transit, while the scalable infrastructure allows for seamless scaling to accommodate massive traffic spikes.
Prerequisites
First, you need to obtain access to the Cubbit Web Console or https://console.[your-tenant].cubbit.eu. You can follow these instructions on how to get started with a Cubbit account.
Installation
Then, you need to register, login into your AWS console and access the CloudFront dashboard.
Cubbit public read permission
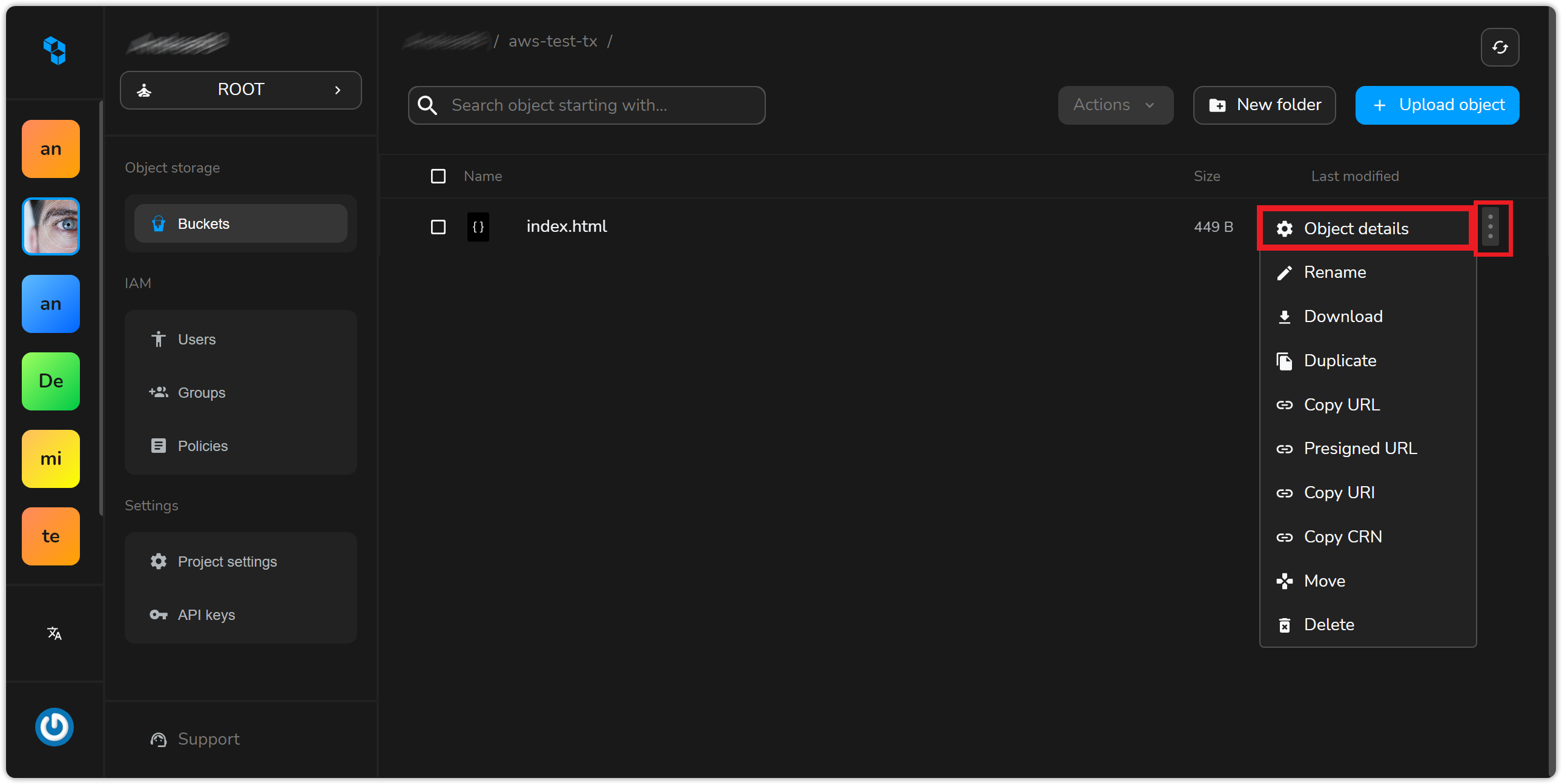
To access an object publicly within an S3 bucket, it is necessary to grant Public READ permissions to the object. The following screenshots illustrate how to assign this permission to the individual object from the Cubbit console. Select “Object details” by clicking on the 3 dots on the right side of the object as below
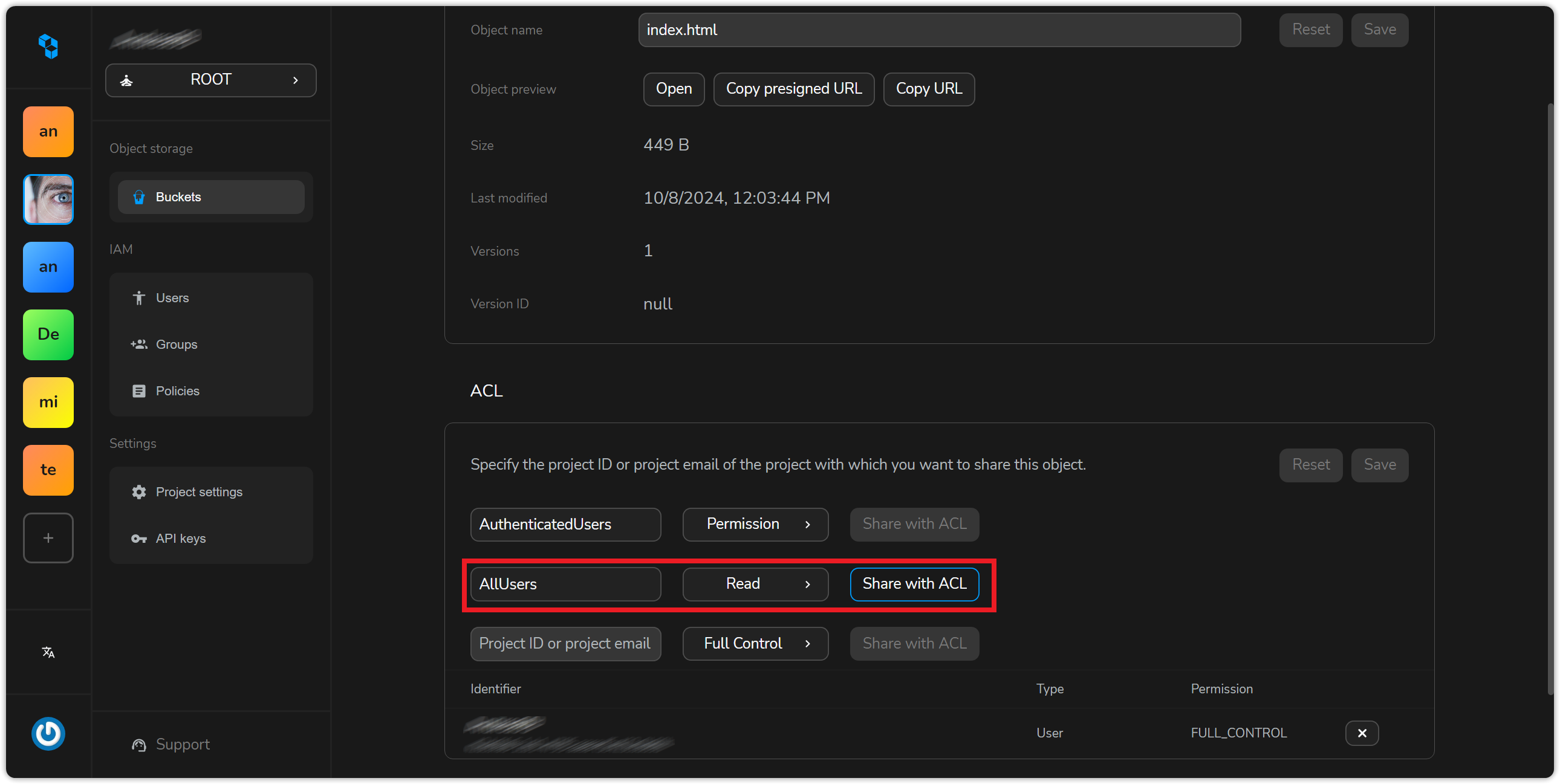
Then on the ACL field, select All Users and Read and select “share with ACL”
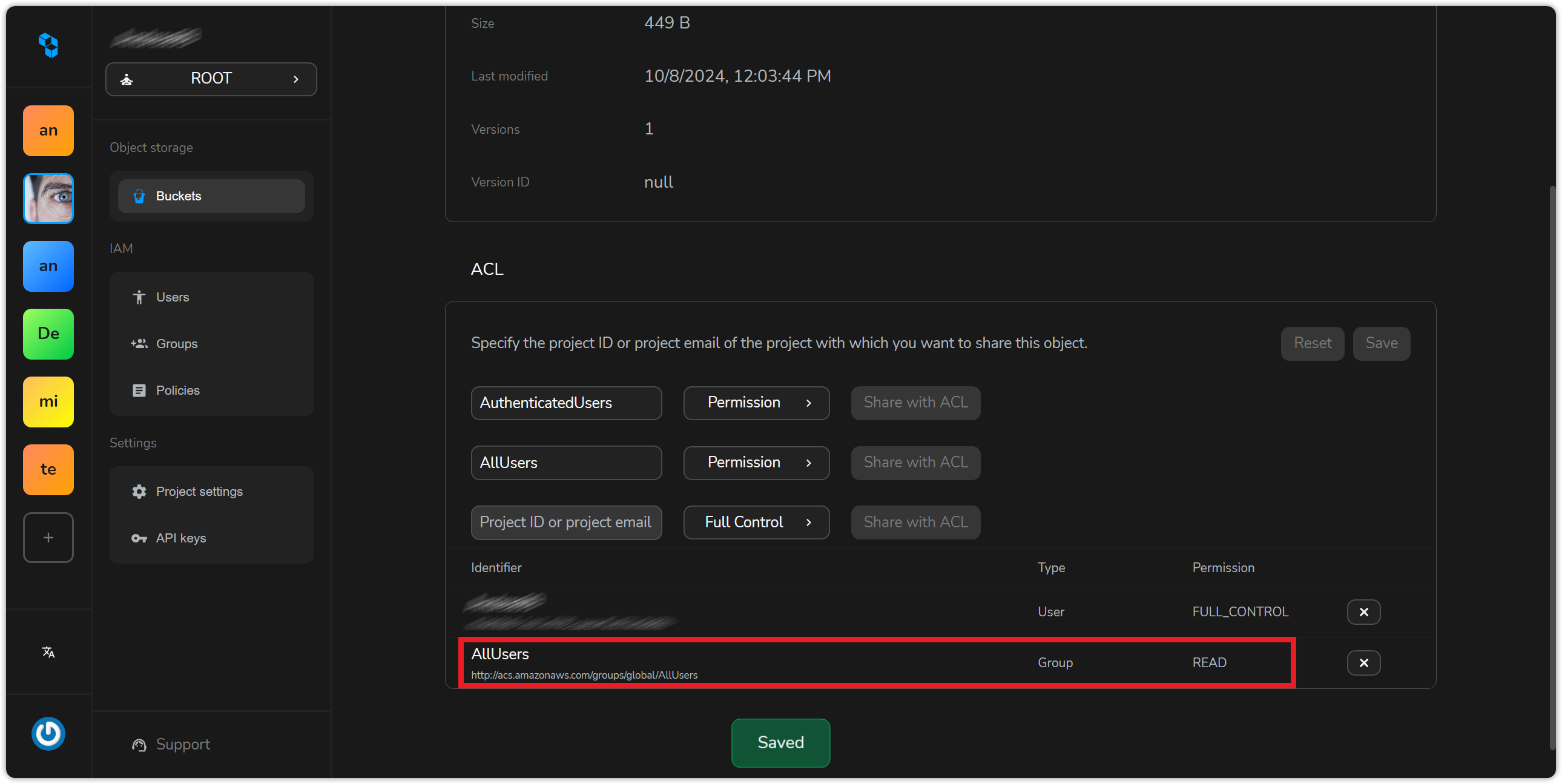
Click on save to apply. You’ll see the permission entry added to the active ACL.
If you prefer you can also give public READ permission on an object with AWS CLI, you can use the AWS s3 command with the put-object-acl subcommand. Here's the basic syntax:
aws s3api put-object-acl --bucket <bucket-name> --key <object-key> --acl public-read
bucket-name is the name of the S3 bucket that contains the object.
object-key is the key (or name) of the object you want to grant public read access to.
Alternatively, you can utilize the --acl public-read option with the cp command to simultaneously upload an object and set its permissions to publicly readable.
aws s3 cp index.html s3://aws-test-tx --endpoint-url=https://s3.cubbit.eu --acl public-read
This command will update the Access Control List (ACL) of the specified object to allow public read access. We can now reach our object publicly on the web.
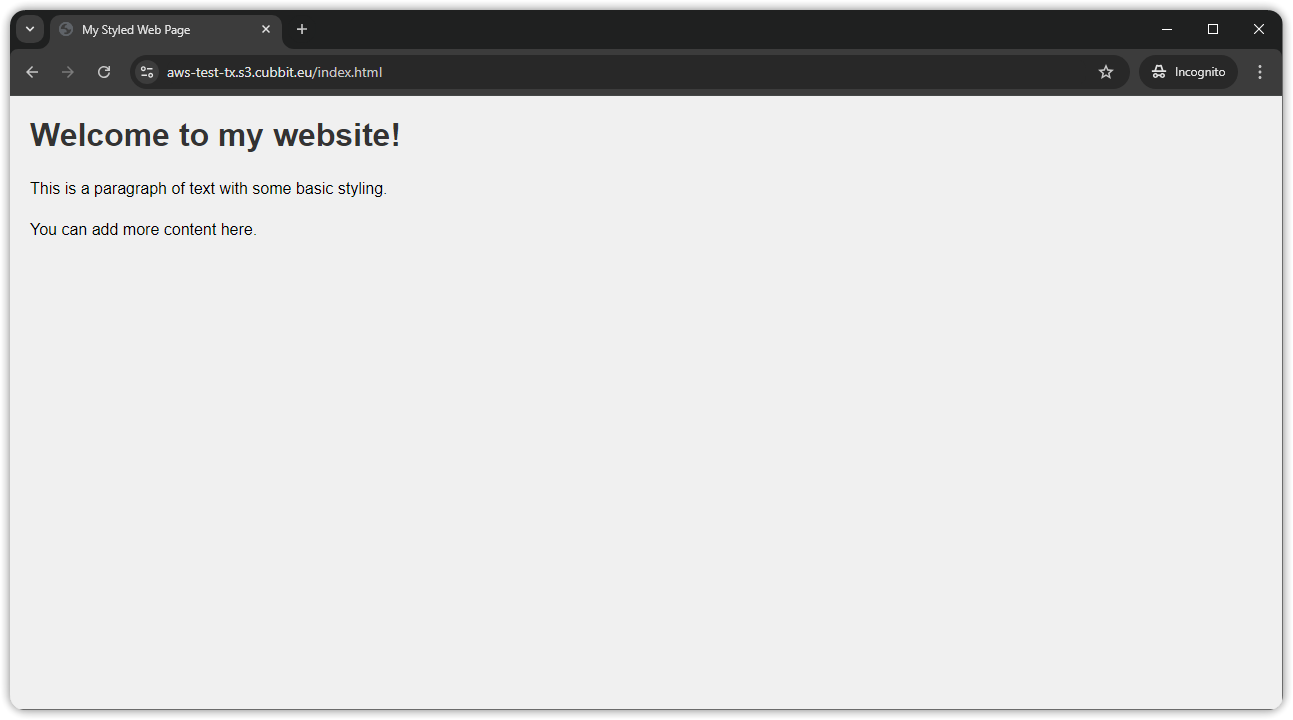
AWS CloudFront
To initiate the setup process for CloudFront, navigate to the CloudFront dashboard within the AWS Management Console. From there, click on 'Create distribution' and proceed with the configuration as follows:
Don't forget to change the bucket used in the screenshots to the one you will actually be using.
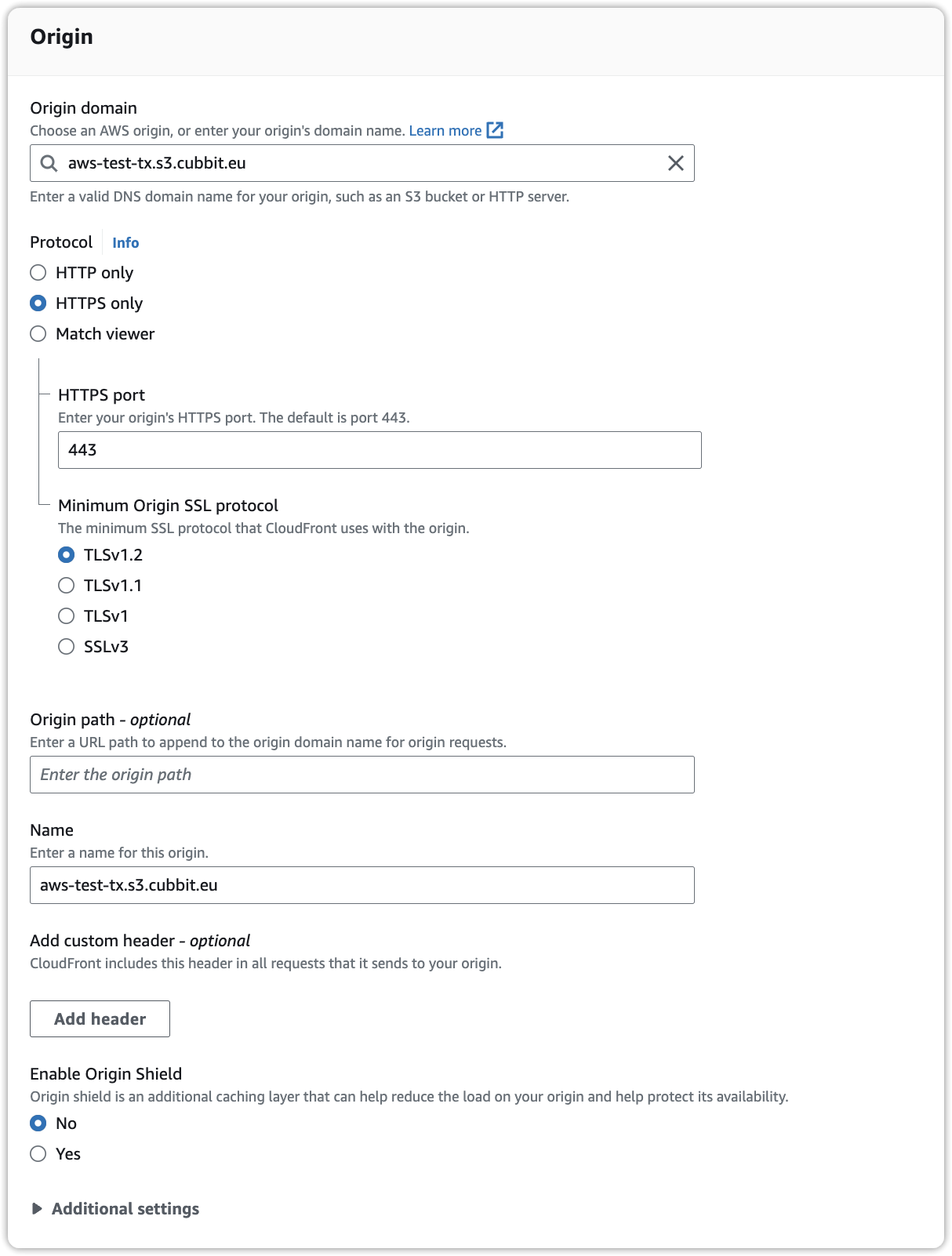
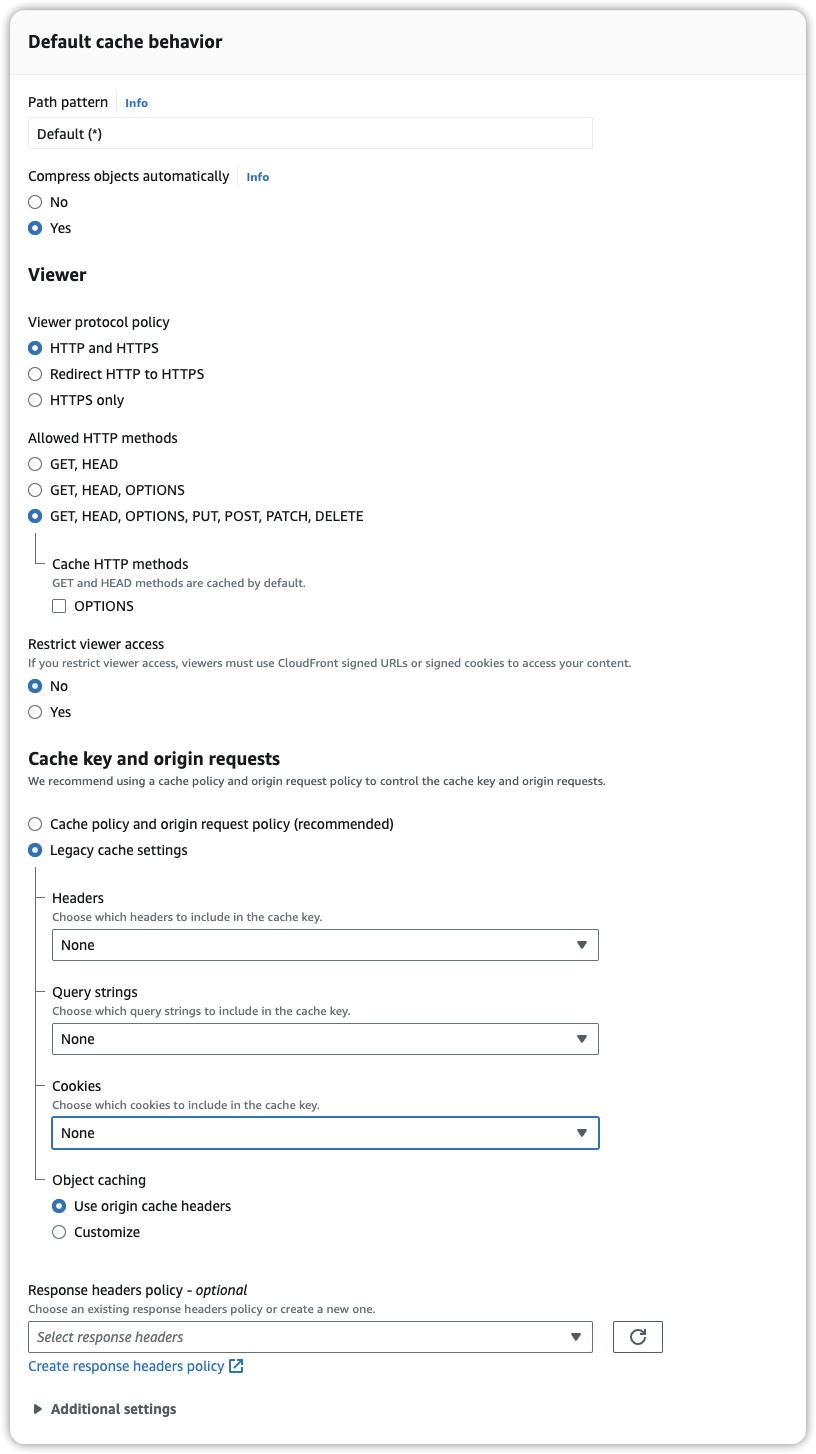
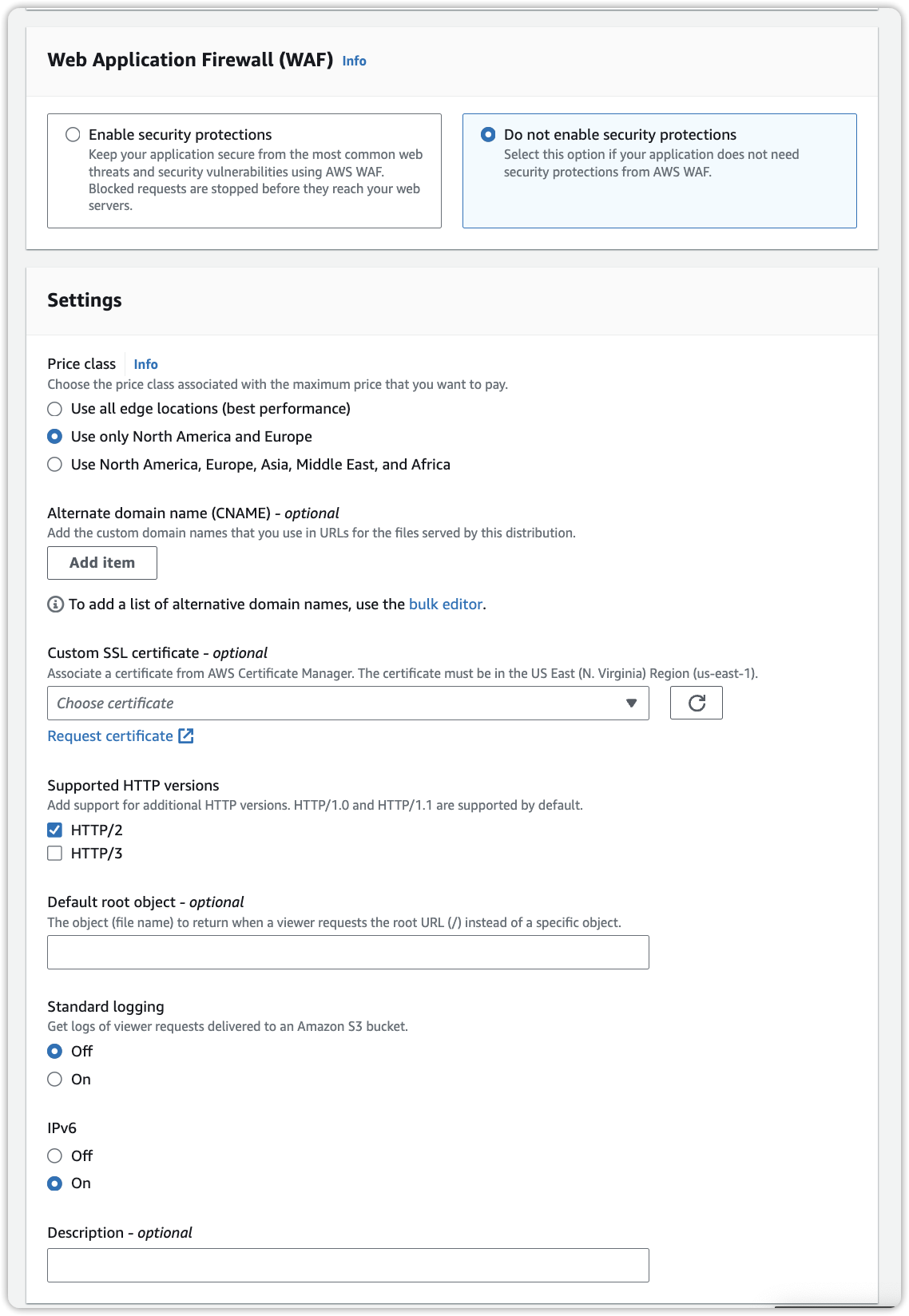
Congratulations! You can now access objects with public read permissions through the newly configured CloudFront distribution.
Remember to:
Choose the right origin: make sure to choose the right origin for your CDN distribution based on your geographical location and user needs.
Optimize Cache Behavior: Configure cache behaviors to control how CloudFront caches your content. You can set different caching rules based on the path patterns, which allows you to optimize performance for static assets (like images and scripts) while managing dynamic content differently.
Enable Logging and Monitoring: Enable CloudFront access logs to track requests and monitor usage patterns. This data can help you understand traffic trends, identify performance issues, and make informed decisions about optimizing your distribution settings. Additionally, consider using AWS CloudWatch for real-time monitoring of your distribution's performance.
CloudFront Distribution Security improvement
Security has to be granted to 2x different level:
-
Access to the static content from Cubbit will be served to a list/sub-list of Cloud-Front public IPs only. This is where CDN IP are listed: IP-ranges This will be done by configuring tenant policy access in the nginx section of the Cubbit GW. This avoids directly exposing original content to any user.
-
Access to the content redistributed by Cloud-Front will be regulated by leveraging other AWS services, such as Lambda functions (see example below), following AWS standard and good-practices.
Example:
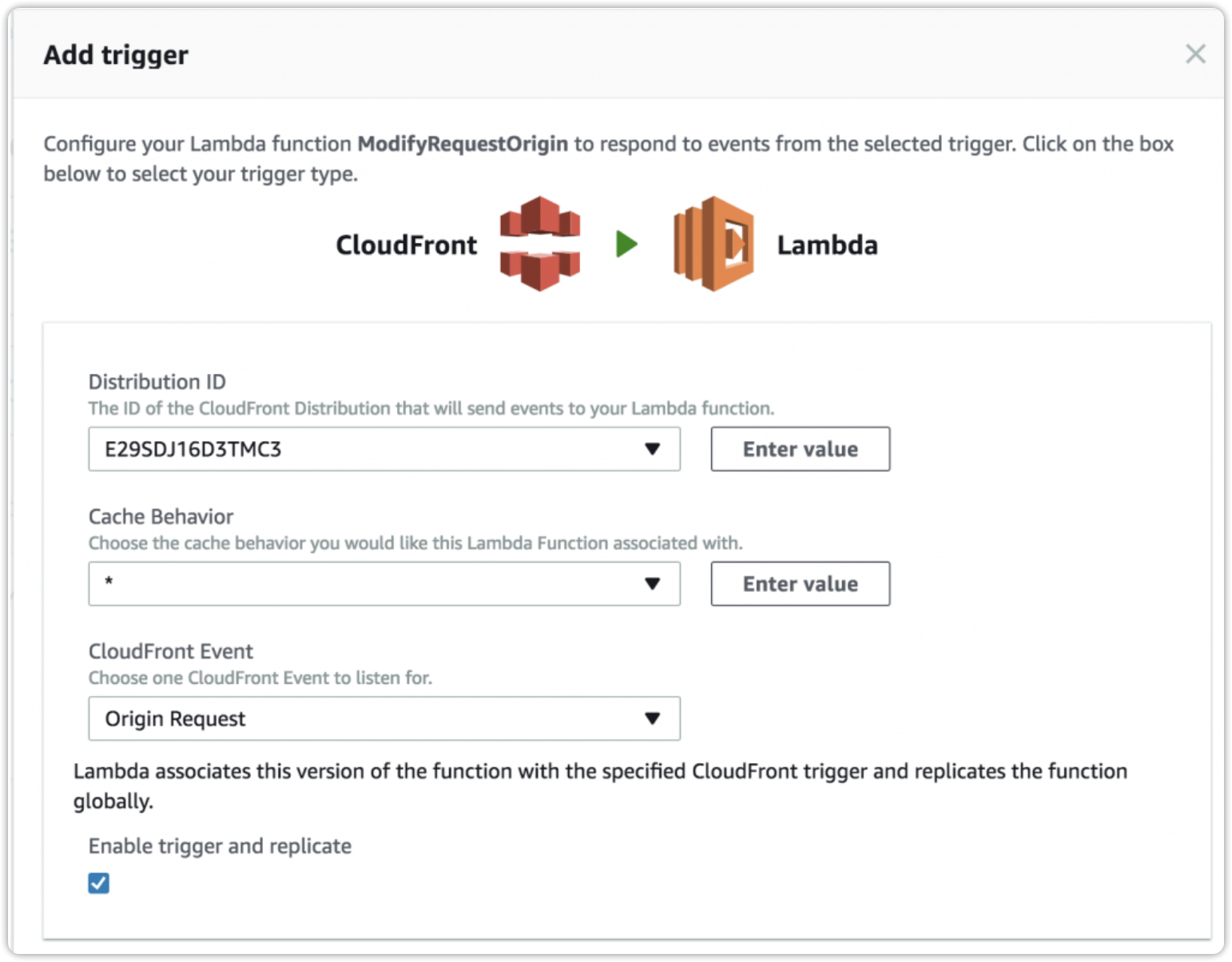
To connect a Lambda function that regulates access to a resource distributed by CloudFront, follow this article.
Create a Lambda@Edge function and associate it with the CloudFront distribution during the viewer request event, the function will be triggered every time a user attempts to access a static resource (such as an image or a video). The Lambda@Edge function will execute to validate the token before serving the resource.
To get detailed information about AWS CloudFront, consult the official AWS CloudFront Knowledge base.