Cloudflare
Intro
Cloudflare is a content delivery network (CDN) and security platform that protects and accelerates websites, APIs, and applications. It acts as a reverse proxy between visitors and websites, filtering out malicious traffic, caching content, and optimizing performance. This guide is intended for users who use Cloudflare's CDN and want to distribute data stored in a Cubbit bucket through Cloudflare's global infrastructure. By integrating Cubbit with Cloudflare, you can enhance content availability, reduce latency, and improve the user experience when accessing files. This guide provides step-by-step instructions to ensure seamless content delivery, offering security, redundancy, and scalability for various data types.
Prerequisites
First, you need to obtain access to the Cubbit Web Console or https://console.[your-tenant].cubbit.eu. You can follow these instructions on how to get started with a Cubbit account.
Installation
Then, you need to register and login into your Cloudflare dashboard.
Cubbit public read permission
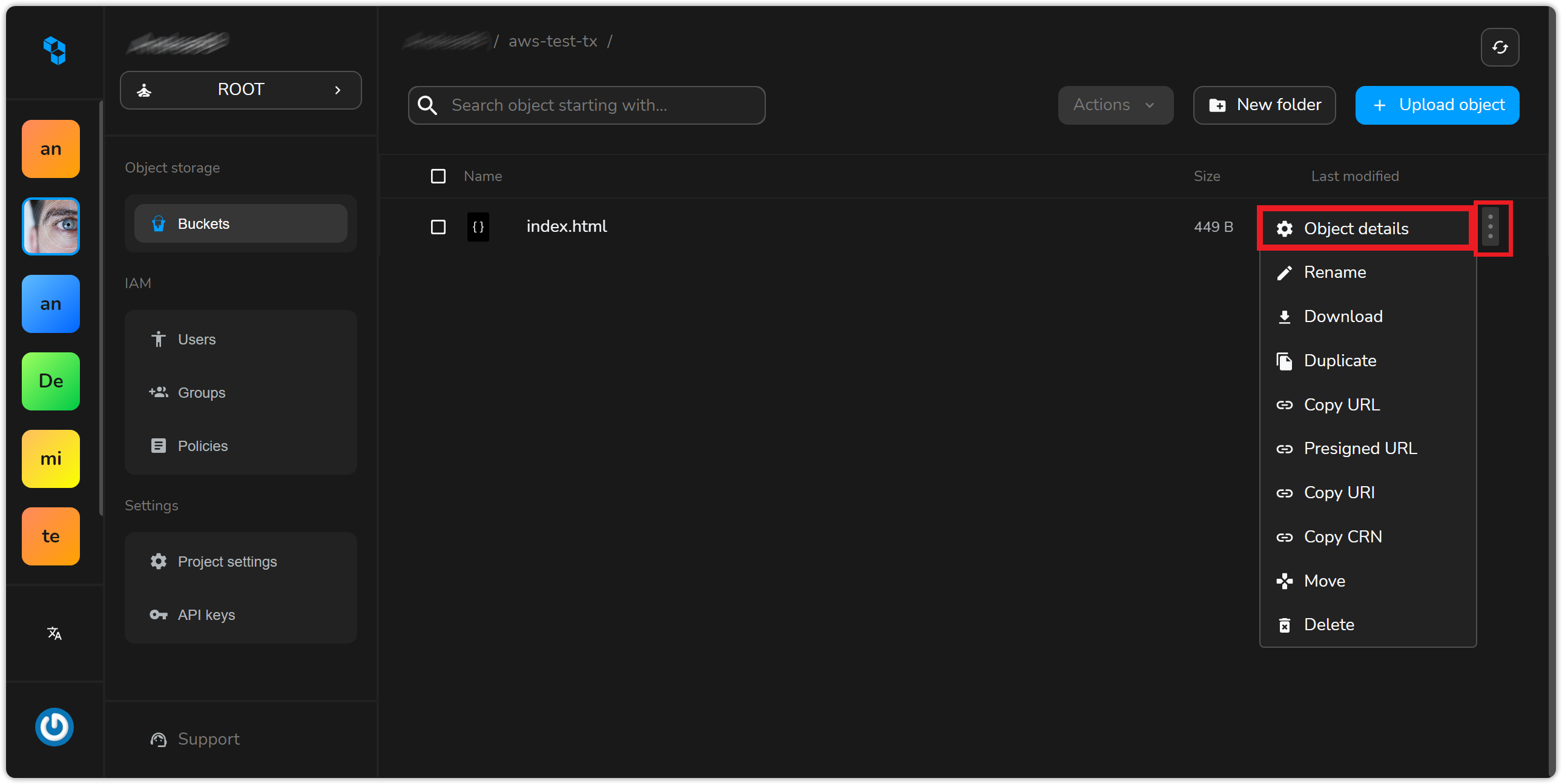
To access an object publicly within an S3 bucket, it is necessary to grant Public READ permissions to the object. The following screenshots illustrate how to assign this permission to the individual object from the Cubbit console. Select “Object details” by clicking on the 3 dots on the right side of the object as below
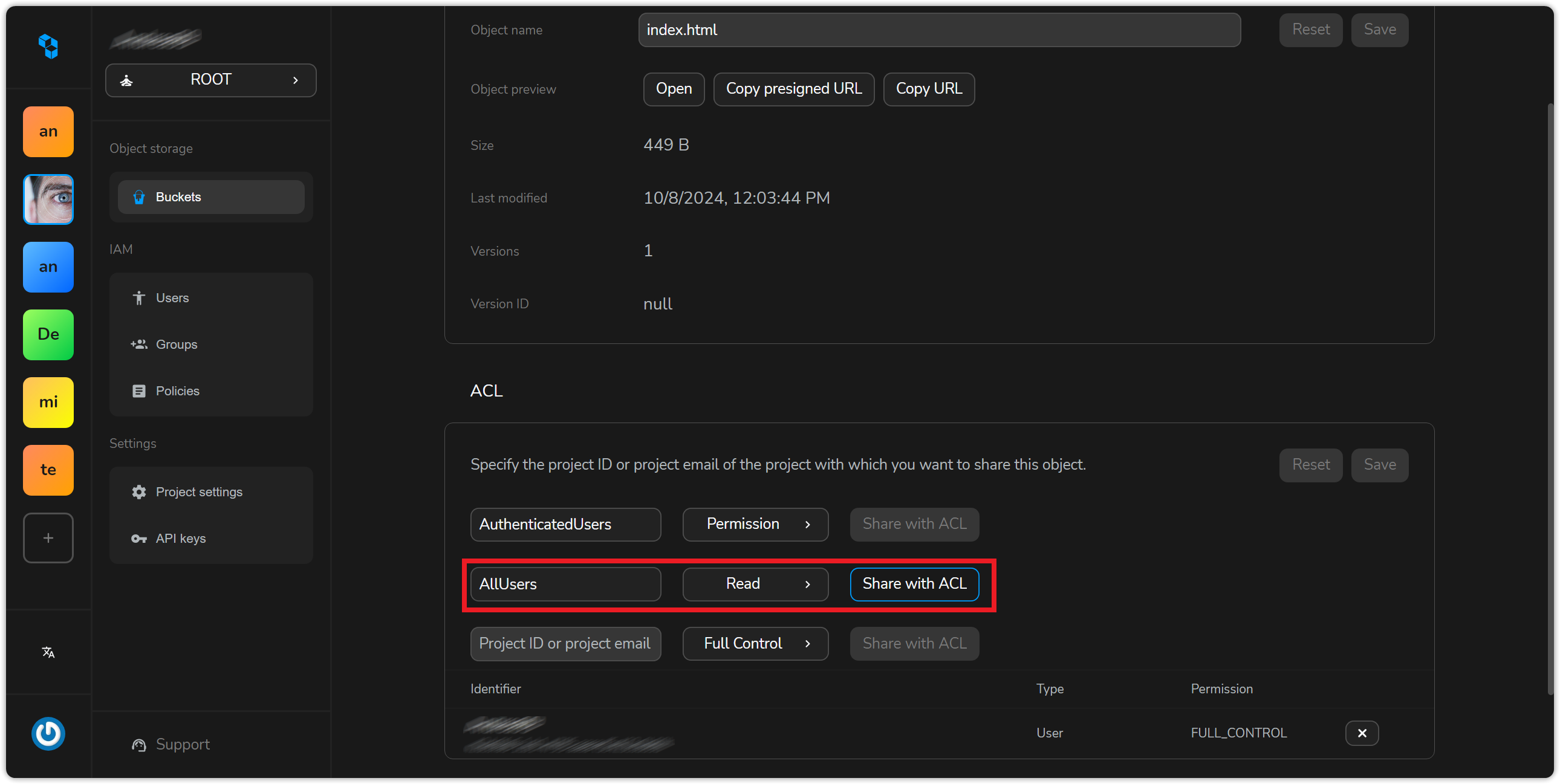
Then on the ACL field, select All Users and Read and select “share with ACL”
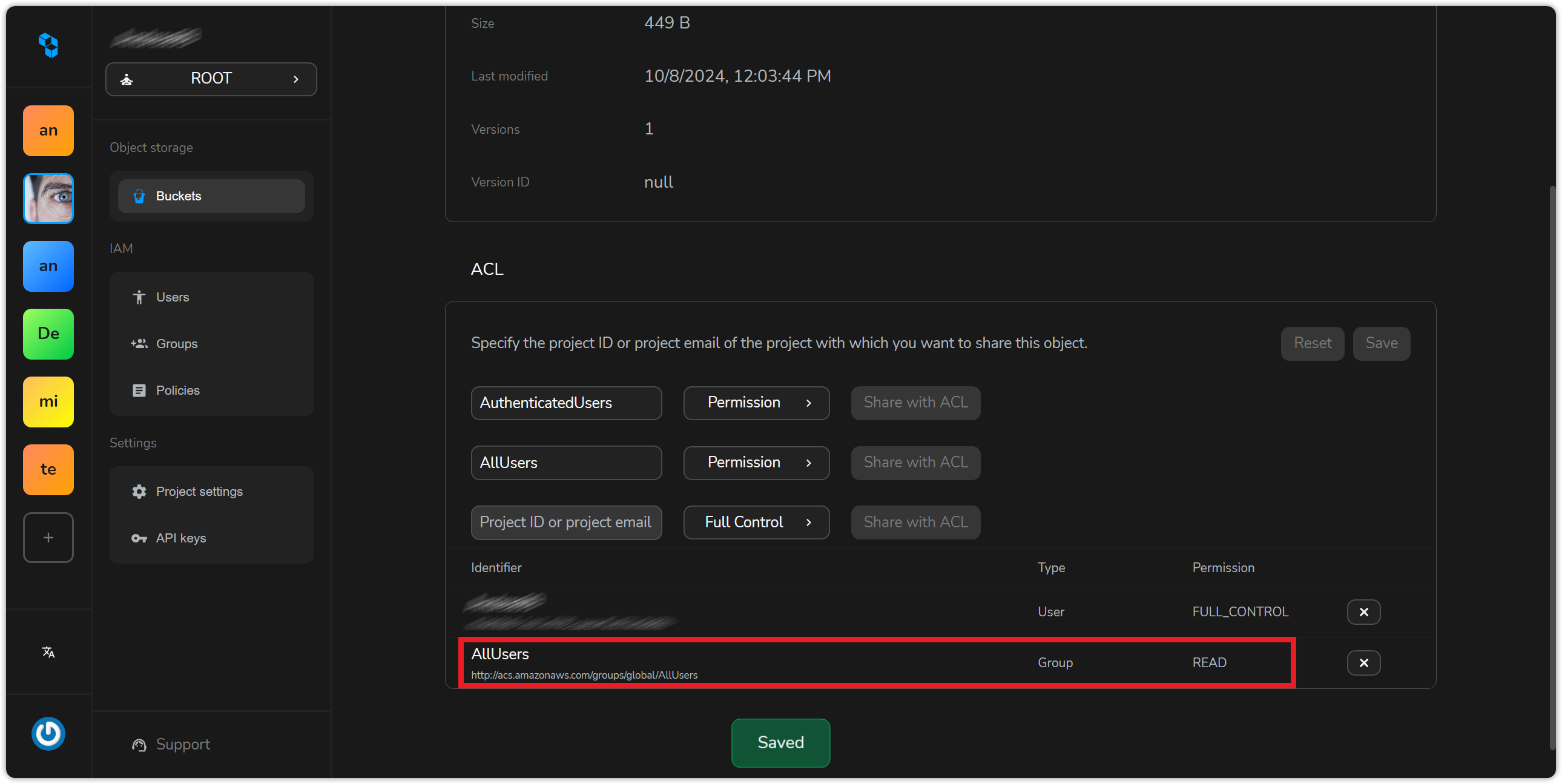
Click on save to apply. You'll see the permission entry added to the active ACL.
If you prefer you can also give public READ permission on an object with AWS CLI, you can use the AWS s3 command with the put-object-acl subcommand. Here's the basic syntax:
aws s3api put-object-acl --bucket <bucket-name> --key <object-key> --acl public-read
bucket-name is the name of the S3 bucket that contains the object.
object-key is the key (or name) of the object you want to grant public read access to.
Alternatively, you can utilize the --acl public-read option with the cp command to simultaneously upload an object and set its permissions to publicly readable.
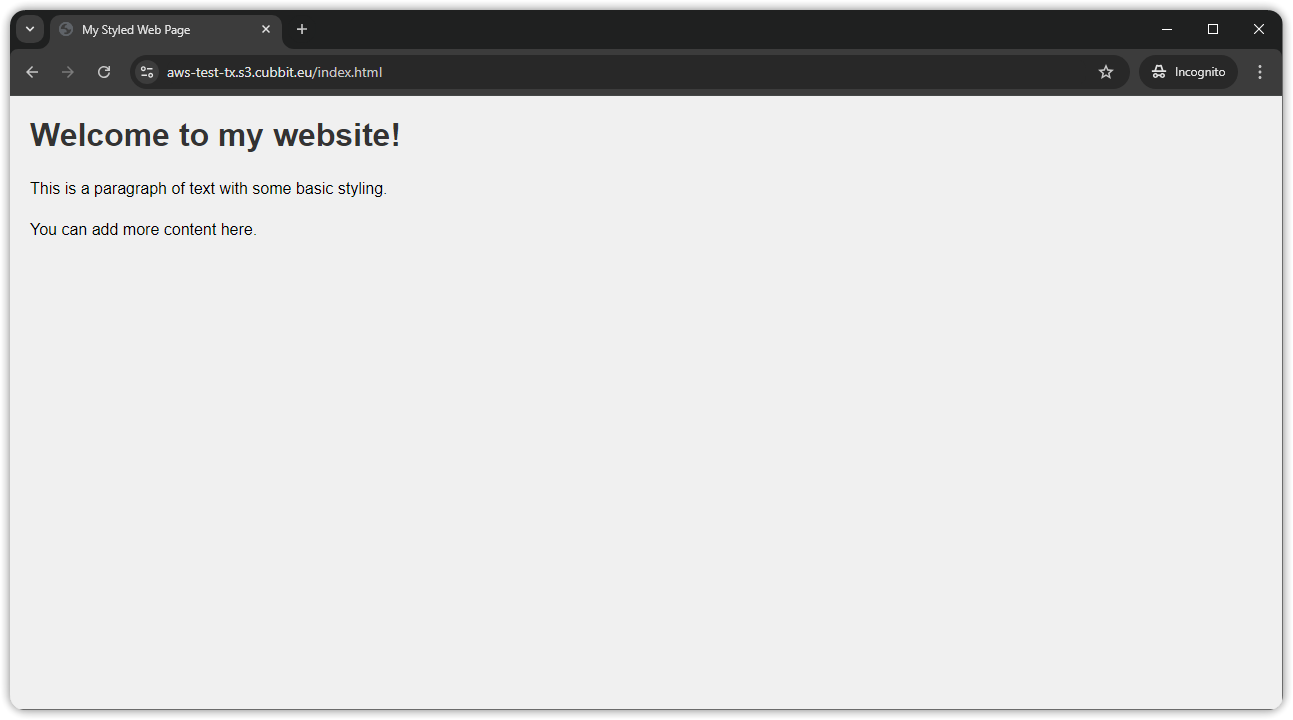
aws s3 cp index.html s3://aws-test-tx --endpoint-url=https://s3.cubbit.eu --acl public-read
This command will update the Access Control List (ACL) of the specified object to allow public read access. We can now reach our object publicly on the web.
Cloudflare
Before starting with Cloudflare configuration make sure that you have at least one domain available managed by Cloudflare.
Set up a Worker to rewrite domain-name
Create a worker by clicking on Workers & Pages menu Create then Create Worker.
Then clicking on “deploy” you can choose a name for your worker (e.g. “cubbit”), edit the code. Replace the preconfigured code with the following:
export default {
async fetch(request, env, ctx) {
const url = new URL(request.url);
url.hostname = 'bucket-name.s3.cubbit.eu';
const modifiedRequest = new Request(url, {
method: request.method,
headers: request.headers,
body: request.body,
redirect: request.redirect,
});
// is it already in CF cache?
let response = await caches.default.match(modifiedRequest);
if (!response) {
response = await fetch(modifiedRequest);
// Valid response:
if (response.ok) {
// 2x stream for the answer
const [stream1, stream2] = response.body.tee();
const clientResponse = new Response(stream1, response);
const cacheResponse = new Response(stream2, response);
// Prepare the headers for CFcache:
cacheResponse.headers.set('Cache-Control', 'public, max-age=31536000');
// put in CF cache:
ctx.waitUntil(caches.default.put(modifiedRequest, cacheResponse));
// Response to client:
return clientResponse;
}
}
// it was in the cache:
return response;
},
};
Replace 'bucket-name' with the name of the bucket you created in the previous paragraph. Alternatively, you can remove it if you wish to keep the bucket as part of the final path exposed by Cloudflare. In that case, CDN resources will be accessible at the URL: mydomain.com/bucketname/
Connect domain to worker
Open the website section, choose “Workers Routes”, then click on "Add route".
Select the domain through which you want to expose the bucket content (e.g., mydomain.com/*). Then, choose the worker you configured in the previous step (cubbit) from the worker drop-down menu.
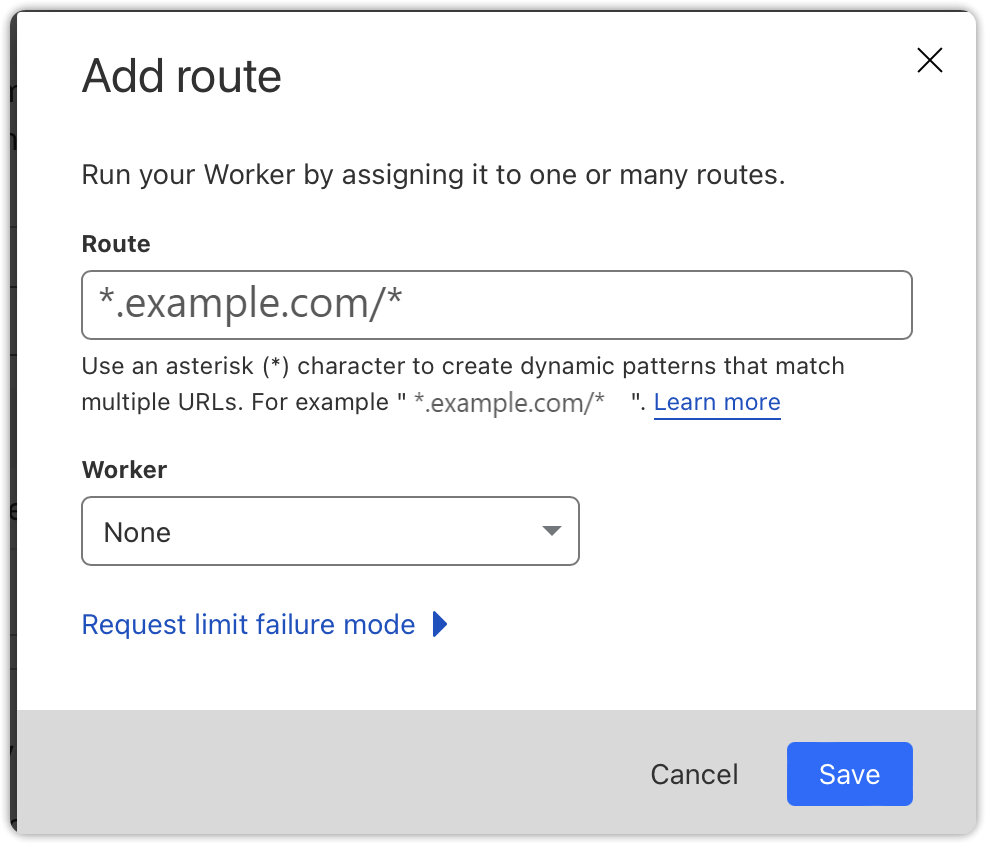
Once the rule is saved, Cloudflare will begin caching and serving your request.
Cloudflare Distribution Security improvement
To enhance security for accessing data stored in the system, it is recommended that access to Cubbit static content will be restricted to a list or sub-list of Cloudflare public IPs only.
This will be enforced by configuring tenant access policies in the nginx section of the Cubbit Gateway, thus preventing direct exposure of original content to users.
Then, an additional level of security (e.g., JWT) can be added to Cloudflare through a specific Worker implementation. This involves validating JWT tokens directly at the edge before allowing access to the resources, enhancing protection by ensuring only authorized requests proceed.
To get detailed information about Cloudflare, consult the official Cloudflare Knowledge base.